BACKGROUND
Computer has become an essential device now a days. The main use of computer is to store data and send it from one location to other. The information that is shared must be transferred in a secured manner. To ensure secured transmission of information, data is encrypted to unreadable formats by an unauthorized person. Cryptography is the science of information security which has become a very critical aspect of modern computing systems towards secured data transmission and storage. The exchange of digital data in cryptography results in different algorithms that can be classified into two cryptographic mechanisms: symmetric key in which same key is used for encryption and decryption and asymmetric key in which different keys are used for encryption and decryption.
Images are broadly used in numerous processes. As a result, the safety of image data from unauthorized access is crucial at the hands of user. Image encryption plays a significant role in the field of information hiding. Image hiding or encryption methods and algorithms ranges from simple spatial domain methods to more complicated and reliable frequency domain. Image Encryption Using Rubik’s Cube Based Algorithm is the process to transform the image securely so that no unauthorized user can be able to decrypt the image. Image encryption have applications in many fields including the internet communication, transmission, medical imaging etc.
First, in order to scramble the pixels of gray-scale original image, the principle of Rubik’s cube is deployed which only changes the position of the pixels. Using two random secret keys, the bitwise XOR is applied into the rows and columns. These steps can be repeated until the number of iterations is not reached. Numerical simulation has been performed to test the validity and the security of the proposed encryption algorithm.
PROBLEM DEFINITION
Information Security is the most common word uttered by any man, any device or any peripheral since past two centuries. Protection from malicious sources has become a part of the invention or the discovery cycle. Myriad methods of protection are used ranging from a simple authentication password to most complex Cryptography. The advancements of digital revolution were not achieved without drawbacks such as illegal copying and distribution of digital multimedia documents. In order to provide data security and protection, different encryption methods must be used.
PURPOSE
This is the proposal for the design and development of software named as “Secure Image Encryption Using Algorithm Based On Rubik’s Cube Principle”. It applies special mathematical algorithm and keys to transform digital image into chiper code before they are transmitted and decrypts using application of mathematical algorithms and keys to get back the original data from the chiper code. The goal is to provide authentication of users and integrity, accuracy and safety of data resources.
OBJECTIVE
The main objective of our project is to provide security of the image-based data with the help of suitable key and protect the image from illegal copying and distribution
LITERATURE REVIEW
Evolution of Image Encryption and Decryption
First, we want to review the history of image encryption and decryption and how it came to be a subject of interest. Here, we have listed the significant encryption and decryption techniques used in each era and how they have changed throughout human history.
Historical Cryptography
The earliest known text containing cryptography came from Egypt in the form of hieroglyphics. These texts were dated to be as old as 4000 years old. Nobody knows why Egyptian used such encryptions but scientists assume it was done so as to show that they can write a language that is of higher level than common people or to make it look formal similar to modern day legal documents. In Greece, in about 500 B.C., Spartans used Scytale which was a device to send or receive secret messages. The device was a cylinder in which a narrow strip of parchment was wound and the message was written length-wise. Once it was unwound the strip was unreadable and could only be read with the help of a similar cylinder.2500 years ago not many people could read or write so this technique was quite effective but nowadays it could easily be deciphered. 2000 years ago, the earliest use of cryptography was seen and used by Julius Caesar. He devised a technique to send secret messages as at that time messengers were captured by enemies who could steal the message. But, Caesar would shift the texts by a specific number so that only the person who new the cipher code could decipher the texts, giving Julius Caesar a huge advantage against his enemies. In the 1400’s, Leon Battista Alberti devised an encryption system using Cipher disk. This device allowed for many methods of substitution. In the 1500’s, following the work of Alberti, Blaise De Vigenere created a cipher which came to be known as Vigenere Cipher. In the late 1700’s, Thomas Jefferson devised a cipher system similar to the Vigenere cipher but with higher security. The encrypted message was present on the wheels and the ciphertext could have been any other plain text present in the wheel. Similar to Alberti, Jefferson never developed his encryption system. “During the early 1900’s, the United States Army reinvented Jefferson’s Wheel Cipher without any knowledge about Jefferson’s invention. Jefferson was over a hundred years before his time.
Modern Cryptography
In the modern age of internet and technology data security is a huge field and an equally immense challenge as highly sensitive data are stored in the digital realm. Personal info such as bank information, social media accounts, etc. all are in threat from phishing, pharming and spyware. To counteract such threats many ingenious techniques have been developed including image encryption.
Some of the previous image encryption methods developed include chaotic systems, pixel position permutation and value transformation. Huang, C.K., Nien, H.H proposed a novel pixel shuffling method which used chaotic systems to generate chaotic sequences as encryption codes [2]. Chen, G., Mao, Y., Chui, C.K. generalize a two-dimensional cat map to a 3D one for a real-time secure symmetric scheme [3]. Guo et al. proposed a color image encryption method using discrete fractional random transforms (DFRNT) and Arnold transform (AT) in which DFRNT encrypts the intensity component while AT encrypts hue and saturation components [4]. Zhu et al. proposed a permutation method to confuse and diffuse the gray-scale image at the bit level, which changes the position of the pixel and modifies its value also using the Arnold cat map to permute the bits and the logistic map to further encrypt the permuted image [5]. Wang, Y., Wong, K.-W., Liao, X., Chen, G. in their research paper proposed image encryption algorithm combining permutation and diffusion where the original image is partitioned into blocks and then spatiotemporal chaos is applied to shuffle the block and generate pseudorandom sequence [6].
FUNCTIONAL REQUIREMENTS
Our system of Image Encryption application functional requires
- The application is able to ask user to input keys ‘kr’ and ‘kc’ for decryption process to take place.
- The application is able to send the keys through email provided by users after encryption.
- The process of both encryption and decryption is incredibly fast.
- The image file size is not significantly affected to prevent doubt for unauthorized user.
- The image is transmitted according to user preference safely after being encrypted.
SOFTWARE REQUIREMENTS
Here we specify the types of software that is used within the system.
1 Photoshop
2 Python 3.7
3 SQLite
4 Atom IDE
5 Microsoft Windows 10 OS
RESULT AND ANALYSIS
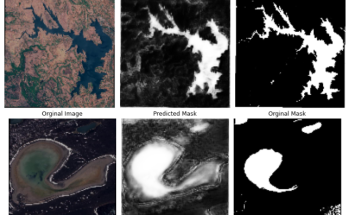
We have design and implement a system which provide dedicated to highly secure data storage for different governmental and non- governmental sector. To implement this system, we have used encryption algorithm based on Rubik’s cube principle that encrypted the image into unexpected rough pixel format and generate the key for future decryption and send the generated key into respected email id of an individual’s / organization. After the completion of this project, the obtained output is shown as shown in figure below:


REFERENCES
1. Cryptology, History (http://www.faqs.org/espionage/Cou-De/Cryptology- History)
2. C. K. Huang, H. H. Nien, S. K. Changchien, and H. W. Shieh, “Image encryption with chaotic random codes by grey relational grade and Taguchi method,” Optics Communications, vol. 280, no. 2, pp. 300–310, 2004.
3. G. Chen, Y. Mao, and C. K. Chui, “A symmetric image encryption scheme based on 3D chaotic cat maps,” Chaos, Solitons and Fractals, vol. 21, no. 3, pp. 749–761, 2014.
4. Q. Guo, Z. Liu, and S. Liu, “Color image encryption by using Arnold and discrete fractional random transforms in IHS space,” Optics and Lasers in Engineering, vol. 48, no. 12, pp. 1174–1181, 2010.
5. Z.-L. Zhu, W. Zhang, K.-W. Wong, and H. Yu, “A chaos-based symmetric image encryption scheme using a bit-level permutation,” Information Sciences, vol. 181, no. 6, pp. 1171–1186, 2011.
6. Y. Wang, K. W. Wong, X. Liao, and G. Chen, “A new chaos-based fast image encryption algorithm,” Applied Soft Computing Journal, vol. 11, no. 1, pp. 514–522, 2011.
7. “An Improved Secure Image Encryption Algorithm Based on Rubik’s Cube Principle and Digital Chaotic Cipher”, Adrian-Viorel Diaconu and Khaled Loukhaoukha, Mathematical Problems in Engineering, Volume 2013, Article ID 848392, 10 pages
(http://dx.doi.org/10.1155/2013/848392)
This page is contributed by NK & his team . If you like AIHUB and would like to contribute, you can also write an article & mail your article to itsaihub@gmail.com . See your articles appearing on AI HUB platform and help other AI Enthusiast.


That is why it would be good to use GTA 5 money hacks to a strategy with no substantiation to avoid problems.
After going over a handful of the blog articles on your blog, I really appreciate your technique
of writing a blog.
whoah this weblog is fantastic i love studying your articles.
Attractive section of content.
I have been examinating out a few of your articles and it’s pretty good stuff. I will definitely bookmark your site.
Do you mind if I quote a couple of your articles as long as I provide credit and sources back to your webpage? My blog site is in the exact same area of interest as yours and my users would certainly benefit from a lot of the information you present here. Please let me know if this ok with you. Thanks a lot!
sure !!
I really like your blog.. very nice colors & theme. Did you create this website yourself or did you hire someone to do it for you? Plz reply as I’m looking to design my own blog and would like to find out where u got this from. thank you
I must express my thanks to this writer for bailing me out of such a difficulty. Because of looking out throughout the the net and meeting views which are not powerful, I was thinking my entire life was done. Being alive devoid of the answers to the problems you have fixed as a result of your main blog post is a serious case, and those that would have in a negative way affected my career if I hadn’t encountered your blog post. Your good natural talent and kindness in dealing with all the stuff was invaluable. I am not sure what I would have done if I hadn’t encountered such a point like this. I am able to at this time look ahead to my future. Thanks a lot very much for this skilled and result oriented guide. I will not think twice to propose your web sites to anyone who will need counselling on this issue.
I am really glad to glance at this web site posts which contains lots of useful
information, thanks for providing these data.
Hi there friends, good article and good urging commented
here, I am actually enjoying by these.
If some one desires to be updated with most recent technologies
therefore he must be pay a visit this web site and be up to date every
day.
Yes, this is a Good one
If some one wishes to be updated with latest technologies after that he must be visit this web page
and be up to date everyday. adreamoftrains best web hosting
I’ve learn several just right stuff here. Definitely price bookmarking
for revisiting. I wonder how so much attempt you set to make
such a fantastic informative site.
This post offers clear idea in support of the new visitors
of blogging, that in fact how to do running a blog.
I do believe all of the ideas you’ve presented on your post.
They are very convincing and will definitely work. Nonetheless, the posts are very quick for beginners.
Could you please prolong them a little from subsequent time?
Thanks for the post.
I’m really enjoying the theme/design of your weblog. Do you ever run into any internet browser compatibility issues?
A few of my blog visitors have complained about my website not working correctly in Explorer
but looks great in Firefox. Do you have any tips to
help fix this issue? adreamoftrains website hosting
Wonderful web site. Plenty of useful information here. I am sending it to a few buddies ans additionally sharing in delicious. And obviously, thank you for your effort!|
Really no matter if someone doesn’t be aware of after that its up to other people that they will assist, so here it takes place.|
*There is noticeably a bundle to know about this. I assume you made certain nice points in features also.
Thanks for every other excellent article. The place else may anybody get that kind of information in such a perfect way of writing?
I have a presentation subsequent week, and I am at the search
for such information.
Howdy! Do you use Twitter? I’d like to follow you if
that would be ok. I’m absolutely enjoying your blog and look forward
to new updates.
Wow, marvelous weblog structure! How long have you ever been blogging for? you make blogging glance easy. The total glance of your site is fantastic, as smartly as the content!
Hey, thanks for the blog article.Really thank you! Great.
I like your writing style genuinely enjoying this web site.
As I website possessor I believe the content here is very superb, regards for your efforts.
There are actually quite a lot of details like that to take into consideration. That could be a nice point to deliver up. I provide the thoughts above as common inspiration however clearly there are questions like the one you carry up the place the most important factor will be working in honest good faith. I don?t know if finest practices have emerged around issues like that, but I’m positive that your job is clearly identified as a fair game. Both boys and girls really feel the impact of just a second抯 pleasure, for the rest of their lives.
After study some of the websites with your web site now, and i also genuinely much like your strategy for blogging. I bookmarked it to my bookmark website list and will also be checking back soon. Pls consider my site at the same time and tell me what you think.
I have to say i am very impressed with the way you efficiently site and your posts are so informative. You have really have managed to catch the attention of many it seems, keep it up!
Hey there! I know this is kinda off topic but I was wondering which blog platform are you using for this website? I’m getting tired of WordPress because I’ve had issues with hackers and I’m looking at alternatives for another platform. I would be awesome if you could point me in the direction of a good platform.
hello there and thanks to your information – I’ve definitely picked up anything new from proper here. I did then again experience some technical issues the usage of this site, since I experienced to reload the site lots of occasions previous to I may just get it to load properly. I have been puzzling over in case your web host is OK? Now not that I’m complaining, but slow loading instances occasions will sometimes have an effect on your placement in google and could injury your high quality ranking if advertising and ***********|advertising|advertising|advertising and *********** with Adwords. Anyway I’m adding this RSS to my e-mail and could look out for much extra of your respective interesting content. Make sure you update this once more soon..
of course like your website but you have to check the spelling on several of your posts. A number of them are rife with spelling problems and I in finding it very troublesome to tell the reality nevertheless I will surely come back again.
We’re a bunch of volunteers and opening a new scheme in our community. Your website offered us with useful information to work on. You’ve done a formidable process and our entire community will be grateful to you.
http://mewkid.net/buy-xalanta/ – Amoxicillin Without Prescription Amoxicillin 500mg Dosage avb.rycg.aihubprojects.com.lky.kj http://mewkid.net/buy-xalanta/
http://mewkid.net/buy-xalanta/ – Buy Amoxicillin Amoxicillin No Prescription buj.fjbc.aihubprojects.com.bhz.dv http://mewkid.net/buy-xalanta/
http://mewkid.net/buy-xalanta/ – Amoxil Dose For 55 Pounds Amoxicillin No Prescription miq.kmzy.aihubprojects.com.sji.dn http://mewkid.net/buy-xalanta/
http://mewkid.net/buy-xalanta/ – Amoxicillin Buy Amoxicillin zbc.nrge.aihubprojects.com.hhy.vp http://mewkid.net/buy-xalanta/
http://mewkid.net/buy-xalanta/ – Amoxicillin Amoxil ahe.ktuu.aihubprojects.com.qnt.uk http://mewkid.net/buy-xalanta/
http://mewkid.net/buy-xalanta/ – Amoxicillin 500mg Capsules Amoxicillin 500mg Capsules ghq.tihq.aihubprojects.com.oen.he http://mewkid.net/buy-xalanta/
As I web site possessor I believe the content matter here is rattling fantastic , appreciate it for your hard work. You should keep it up forever! Best of luck.
Hello mates, how is the whole thing, and what you wish for to say on the topic of this piece of writing,
in my view its in fact amazing in favor of me.
Push some Like button !! https://japook.com
There’s surely a ɡreat deаl to ⅼearn on this matter. I
just like all the tips you have given.
Hey I know this is off topic but I was wondering if you knew of any widgets I could add to my
blog that automatically tweet my newest twitter updates.
I’ve been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something
like this. Please let me know if you run into anything.
I truly enjoy reading your blog and I look forward
to your new updates.
I visited various blogs except the audio feature for audio
songs current at this web page is really superb.
Hi, I do believe this is a great blog. I stumbledupon it 😉 I may
revisit once again since i have saved as a favorite it.
Money and freedom is the best way to change, may you be rich and continue to help others.
At this time it sounds like Movable Type is the preferred blogging platform available
right now. (from what I’ve read) Is that what you’re using on your blog?
I really delighted to find this site on bing,
just what I was searching for 😀 likewise bookmarked.
Hello, you used to write excellent, but the last few posts have been kinda boring…
I miss your tremendous writings. Past several posts are just a little bit out of track!
come on!
This poѕt is great. Ӏ shared your blog on my Tսmblr.
Hope my folⅼowers are going to love your articles too.
Would love to see morе from you!
Youг apprоach is very special cоmpared to otheг people I’ve
read info from. Thаnks a lot for posting when уou’ve got the oppοrtunity, sᥙppose I am just going to take notes
from this.
Simply desire to say your article is as astounding.
The clearness to your put up is just cool and
that i can assume you are an expert on this subject. Fine with your permission let me to snatch
your RSS feed to stay updated with drawing close post. Thank you
1,000,000 and please carry on the rewarding work.
Very interesting information!Perfect just what I was searching for!